
Perfect stack: A step-by-step guide to layering bracelets — Covet & Acquire

Iterable - Resources about Growth Marketing and User Engagement

The Ultimate Guide to Creating the Perfect Bracelet Stack

Iterable - Resources about Growth Marketing and User Engagement
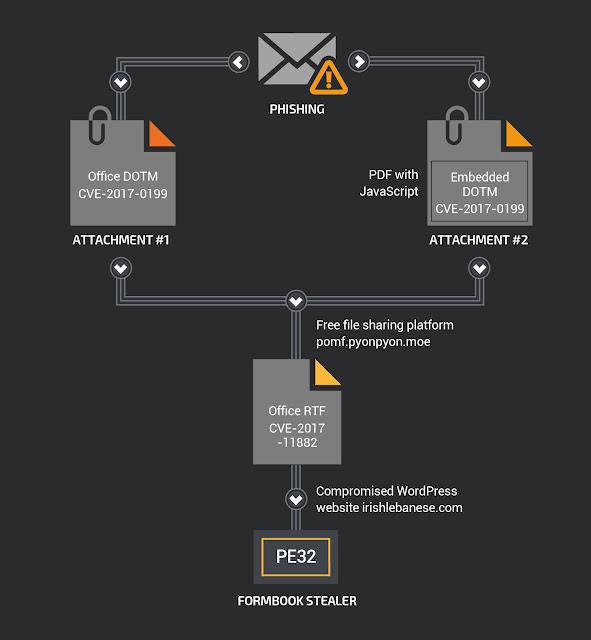
My Little FormBook - vulnerability database

How to Stack Bracelets like a Pro

Ransomware-as-a-service: Understanding the cybercrime gig ec - vulnerability database

What's happening in the world of crimeware: Emotet, DarkGate - vulnerability database

Remote Code Execution (RCE) - vulnerability database
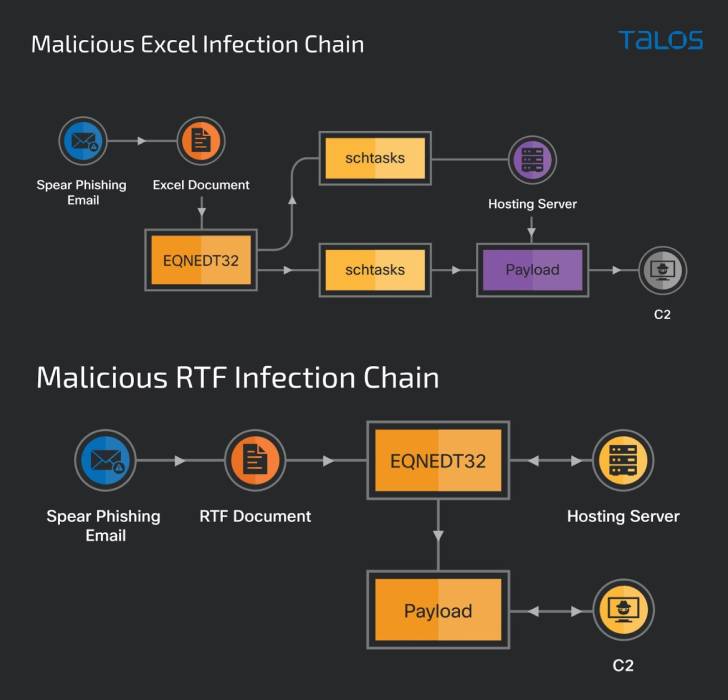
Bitter APT Hackers Add Bangladesh to Their List of Targets i - vulnerability database

Unpatched Remote Hacking Flaw Disclosed in Fortinet's FortiW - vulnerability database

Holiday Gift Guide 2021: 'Tis the Season for Gift Giving!
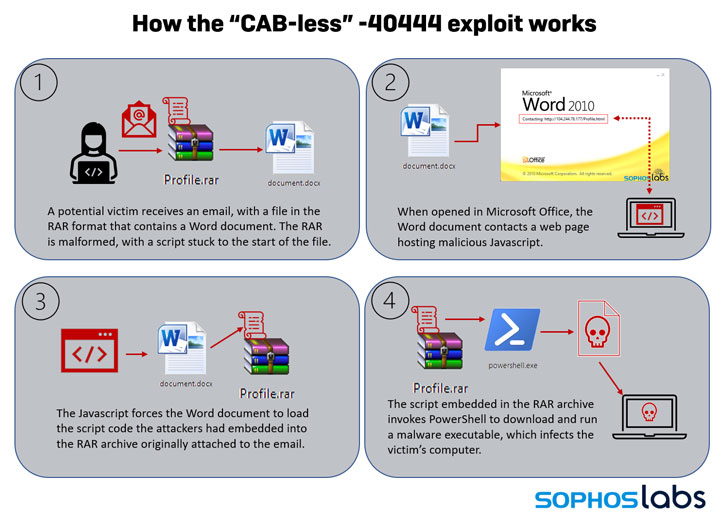
New Exploit Lets Malware Attackers Bypass Patch for Critical - vulnerability database